搜索结果: 1-15 共查到“IDENTITY”相关记录542条 . 查询时间(0.088 秒)
Single-cell transcriptomics sheds light on the identity and metabolism of developing leaf cells
Single-cell transcriptomics photosynthetic Arabidopsis thaliana high-throughput transcriptome metabolic stress-related
2023/11/30
As the main photosynthetic instruments of vascular plants, leaves are crucial and complex plant organs. A strict organization of leaf mesophyll and epidermal cell layers orchestrates photosynthesis an...
Academy of Mathematics and Systems Science, CAS Colloquia & Seminars:On the Pleijel identity
Pleijel恒等式 光滑边界 Blaschke–Petkantschin
2023/10/16

Neurons stripped of their identity are hallmark of Alzheimer's disease, study finds(图)
Neurons stripped hallmark Alzheimer disease
2020/11/20
Researchers at the University of California San Diego have identified new Alzheimer's disease mechanisms in neurons. The scientists have discovered that changes in the structure of chromatin...

Identity of mystery Florida invader corrected after 20 years(图)
Identity mystery Florida invader corrected 20 years
2020/1/19
Sometimes scientists make mistakes. A case in point is the chanchita, a South American non-native freshwater fish that has been swimming in Florida's waters for at least two decades, all the while mis...
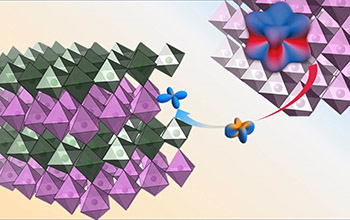
Iridium 'loses its identity' when interfaced with nickel(图)
Iridium loses identity interfaced nickel
2019/10/17
Note to physicists and materials scientists: You'd better reevaluate your work if you study iridium-based materials -- members of the platinum family -- when they are ultra-thin.Iridium "loses its ide...
CCA-Secure Leakage-Resilient Identity-Based Key-Encapsulation from Simple (not $\mathtt{q}$-type) Assumptions
public-key cryptography leakage-resilient identity-based encryption
2019/8/30
In this paper, we propose a new leakage-resilient identity-based encryption (IBE) scheme that is secure against chosen-ciphertext attacks (CCA) in the bounded memory leakage model. It is the first CCA...

Environmental change is triggering an identity switch in grasslands(图)
Environmental change triggering identity switch grasslands
2019/10/21
Since the first Homo sapiens emerged in Africa 300,000 years ago, grasslands have sustained humans and thousands of other species. Today, those grasslands are shifting. Global change -- including clim...
Simplified Revocable Hierarchical Identity-Based Encryption from Lattices
Lattices Identity-based encryption Revocation
2019/8/14
As an extension of identity-based encryption (IBE), revocable hierarchical IBE (RHIBE) supports both key revocation and key delegation simultaneously, which are two important functionalities for crypt...
We design a suite of protocols so that a small tamper-resistant device can be used as a biometric identity document which can be scanned by authorized terminals. We target both strongly secure identif...
A Generic Construction for Revocable Identity-Based Encryption with Subset Difference Methods
Revocable identity-based encryption Subset difference method Generic construction
2019/7/15
To deal with dynamically changing user's credentials in identity-based encryption (IBE), providing an efficient key revocation method is a very important issue. Recently, Ma and Lin proposed a generic...
Identity-Based Encryption from e-th Power Residue Symbols
identity-based encryption ee-th power residue symbol the general reciprocity law on function fields
2019/5/27
This paper generalizes the notable Galbrath's test by introducing the general reciprocity law on function fields. With the help of the extended Galbrath's test, we show the scheme of Boneh, LaVigne an...
A Generic Construction of Revocable Identity-Based Encryption
Generic Construction Revocable Identity-Based Encryption
2019/3/21
Revocable identity-based encryption (RIBE) is an extension of IBE that supports a key revocation mechanism, which is important when deployed an IBE system in practice. Boneh and Franklin presented the...
After two decades of research on signcryption, recently a new cryptographic primitive, named higncryption, was proposed at ACM CCS'16. Higncryption can be viewed as privacy-enhanced signcryption, whic...
Leakage-resilient Identity-based Encryption in Bounded Retrieval Model with Nearly Optimal Leakage-Ratio
Leakage-resilience Bounded retrieval model Identity-based Encryption
2019/1/26
We propose new constructions of leakage-resilient public-key encryption (PKE) and identity-based encryption (IBE) schemes in the bounded retrieval model (BRM). In the BRM, adversaries are allowed to o...
Deterministic Identity-Based Encryption from Lattice-Based Programmable Hash Functions with High Min-Entropy
deterministic identity-based encryption adaptively secure auxiliary-input
2019/1/26
There only exists one deterministic identity-based encryption (DIBE) scheme which is adaptively secure in the auxiliary-input setting, under the learning with errors (LWE) assumption. However, the mas...


