搜索结果: 1-15 共查到“Run-out”相关记录113条 . 查询时间(0.125 秒)

Gravitational-wave detectors start next observing run to explore the secrets of the universe(图)
引力波探测器 引力波 宇宙观测
2023/6/9
Moving backward is a critical skill in almost every sport. Outfielders need backward speed to chase down fly balls; defensive backs need it to stay with lightning-fast wideouts; and point guards need ...

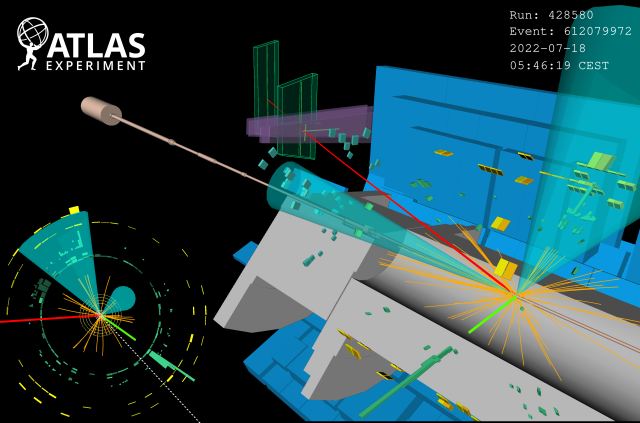
The BRIL luminosity sub-detectors prepare CMS for a bright Run 3(图)
BRIL 亮度子探测器 BRIL子系统 CMS实验
2023/5/30

2018年11月8日上午,由南京大学校牵头,物理学院金山教授主持的国家重点研发计划大科学装置前沿研究重点专项“ATLAS实验Run-2数据物理分析”项目启动会,在我校鼓楼校区顺利召开。科技部高技术研究发展中心墨宏山处长,校长助理陈建群教授,科技处处长徐夕生教授,物理学院院长李建新教授,项目责任专家北京大学朱世琳教授,项目组专家北京大学赵光达院士、中国科学院理论物理研究所张肇西院士、中国科学院上海应...
Study:Mountaintop Coal Mining Causes Appalachian Rivers to Run ‘Consistently Saltier’
Mountaintop Coal Mining Appalachian Rivers Consistently Saltier
2017/7/25
Mountaintop-removal coal mining causes many streams and rivers in Appalachia to run consistently saltier for up to 80 percent of the year, a new study by researchers at the University of Wyoming and D...
The 2nd International Workshop on Models@run.time for Self-aware Computing Systems
International Workshop Self-aware Computing Systems
2017/6/22
In order to most effectively use models at runtime, self-aware computing systems need increasingly powerful ways of observing their operational environment and their own performance and behavior and t...
Electrolytes Made from Liquefied Gas Enable Batteries to Run at Ultra-low Temperatures
Electrolytes Liquefied Gas Batteries to Run Ultra-low Temperatures
2017/7/21
Engineers at the University of California San Diego have developed a breakthrough in electrolyte chemistry that enables lithium batteries to run at temperatures as low as -60 degrees Celsius with exce...
Discovery could lead to jet engines that run hotter—and cleaner
jet engines run hotter cleaner
2017/2/16
Researchers here have made a discovery in materials science that sounds likesomething from the old Saturday morning cartoon Super Friends: They’ve found a way to deactivate “nano twins” to impro...
INTEGRATING GEO-SPATIAL DATA FOR REGIONAL LANDSLIDE SUSCEPTIBILITY MODELING IN CONSIDERATION OF RUN-OUT SIGNATURE
Classification Data Mining Geo-Spatial Data Landslide Susceptibility Random Forests Run-out Typhoon Morakot
2016/11/30
This study implements a data mining-based algorithm, the random forests classifier, with geo-spatial data to construct a regional and rainfall-induced landslide susceptibility model. The developed mod...
Roach-like robots run,climb and communicate with people
Roach robots run climb communicate people
2016/6/12
Insects make themselves at home in the most unwelcoming terrain: on steep inclines, in dark crevices, under shaky rubble.While their ability to go just about anywhere can be disturbing at times, elect...
Design in Type-I, Run in Type-III: Fast and Scalable Bilinear-Type Conversion using Integer Programming
Conversion Bilinear Groups Integer Programming
2016/6/6
Bilinear-type conversion is to convert cryptographic schemes designed over symmetric groups instantiated with imperilled curves into ones that run over more secure and efficient asymmetric groups. In ...
Using the Run-Time Sizes of Data Structures to Guide Parallel Thread Creation
Run-Time Sizes Data Structures Guide Parallel Thread Creation
2016/5/24
Dynamic granularity estimation is a new technique for automatically identifying expressions in functional languages for parallel evaluation. Expressions with little computation relative to thread-crea...
Children of War:The Long-Run Effects of Large-Scale Physical Destruction and Warfare on Children
Children of War Long-Run Large-Scale Physical Destruction Warfare Children
2016/3/3
This paper provides causal evidence on the long-term consequences of large-scale physical destruction on educational attainment, health status, and labor market outcomes of children. I exploit the pla...
Side-Channel Watchdog: Run-Time Evaluation of Side-Channel Vulnerability in FPGA-Based Crypto-systems
Side-Channel Vulnerability FPGA-Based Crypto-systems
2016/2/24
Besides security against classical cryptanalysis, its important
for cryptographic implementations to have sufficient robustness against
side-channel attacks. Many countermeasures have been proposed ...


