搜索结果: 1-15 共查到“perfect”相关记录146条 . 查询时间(0.062 秒)
Academy of Mathematics and Systems Science, CAS Colloquia & Seminars:The complexity of computing Markov perfect equilibrium in general-sum stochastic games
一般 随机博弈 马尔可夫完美均衡 计算复杂性
2023/5/12

MIT engineers grow “perfect” atom-thin materials on industrial silicon wafers(图)
工业硅晶圆 原子薄材料 芯片
2023/6/6
Academy of Mathematics and Systems Science, CAS Colloquia & Seminars:Perfect Matchings in hypergraphs
超图 完美匹配 图论
2023/4/27

Perfect Planks: How to Make this Classic Exercise More Effective(图)
Strength Training Latissimus Dorsi Planks
2024/12/11
To make the Plank more applicable to your sport, here are three critical things to remember when performing this classic exercise.
Graphene is perfectly selective to protons and blocks even smallest ions like chlorine, University of Manchester research shows. This result will be important for the development of graphene-based mem...
Graphene is perfectly selective to protons and blocks even smallest ions like chlorine, University of Manchester research shows. This result will be important for the development of graphene-based mem...
On Perfect Correctness in (Lockable) Obfuscation
Obfuscation Lockable Obfuscation Perfect Correctness
2019/9/16
In a lockable obfuscation scheme a party takes as input a program PP, a lock value αα, a message mm and produces an obfuscated program P~P~. The obfuscated program can be evaluated on an input xx to l...
On Perfect Correctness without Derandomization
Indistinguishability Obfuscation Correctness Functional Encryption
2019/9/16
We give a method to transform any indistinguishability obfuscator that suffers from correctness errors into an indistinguishability obfuscator that is perfectlyperfectly correct, assuming hardness of ...

Perfect timing:Making the 'switch' from juvenile to adult(图)
Perfect timing Making switch juvenile adult
2019/10/23
Very little is known about how the onset of puberty is controlled in humans, but an NSF-funded discovery of a new gene in the roundworm C. elegans could be the "missing link" that determines the juven...
It has been 70 years since the publication of the seminal outstanding work of Claude Elwood Shannon, in which he first gave a mathematical definition of the cryptosystem and introduced the concept of ...
Symmetric-key Authenticated Key Exchange (SAKE) with Perfect Forward Secrecy
Authenticated key agreement Symmetric-key cryptography Perfect forward secrecy
2019/5/9
Key exchange protocols in the asymmetric-key setting are known to provide stronger security properties than protocols in symmetric-key cryptography. In particular, they can provide perfect forward sec...
Teleportation-based quantum homomorphic encryption scheme with quasi-compactness and perfect security
quantum cryptography quantum encryption delegated quantum computation
2018/12/20
Quantum homomorphic encryption (QHE) is an important cryptographic technology for delegated quantum computation. It enables remote Server performing quantum computation on encrypted quantum data, and ...
Perfect Secure Computation in Two Rounds
MPC MPRE
2018/11/9
We show that any multi-party functionality can be evaluated using a two-round protocol with perfect correctness and perfect semi-honest security, provided that the majority of parties are honest. This...
Towards Fully Automated Analysis of Whiteboxes: Perfect Dimensionality Reduction for Perfect Leakage
whitebox cryptanalysis security evaluation
2018/1/29
Differential computation analysis (DCA) is a technique recently introduced by Bos et al. and Sanfelix et al. for key recovery from whitebox implementations of symmetric ciphers. It consists in applyin...
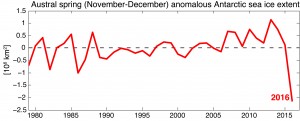
Record-low 2016 Antarctic sea ice due to ‘perfect storm’ of tropical,polar conditions(图)
record-low 2016 antarctic sea ice perfect storm tropical polar conditions
2017/9/19
While winter sea ice in the Arctic is declining so dramatically that ships can now navigate those waters without any icebreaker escort, the scene in the Southern Hemisphere is very different. Sea ice ...


